What is the purpose of device fingerprinting and why is stability important?
Device fingerprinting serves as a powerful tool in various scenarios such as identity verification, transaction fraud prevention, and promotion abuse detection. Its primary objective is to establish and maintain a globally unique identifier, known as the device ID, for a physical device within a specific range. The stability of the device ID plays a crucial role in assessing the effectiveness of this tool. To ensure stability, two key characteristics are essential: restoration capability and uniqueness guarantee. Restoration capability refers to the device fingerprint's ability to restore the original device ID even when the device's state has changed. On the other hand, the uniqueness guarantee ensures that each device possesses a distinct identity code, preventing device IDs from being shared among different devices within the system.
How has the assurance of these two characteristics evolved over time?
Device fingerprinting has undergone a remarkable evolution over the years, driven by the need for better user experience, heightened security, and increased applicability. In this context, TrustDecision, our cutting-edge device fingerprinting solution, has emerged as a leader in the industry, offering unique advantages that set it apart from conventional approaches.
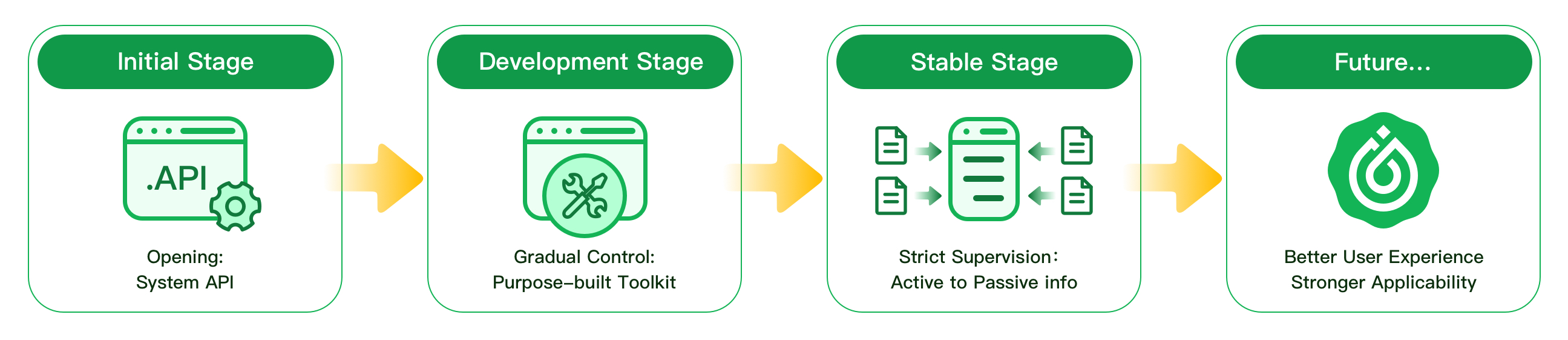
The Initial Stage of Opening: Embracing Openness
During the early days, the environment was characterized by openness. Device manufacturers would preconfigure network access identifiers like IMEI, UUID, and physical MAC addresses into the system. Accessing these identifiers was straightforward for application developers through designated APIs. Although these identifiers were bound by official agreements and demonstrated uniqueness, they were susceptible to manipulation by malicious individuals. This period witnessed relatively low costs for black production attacks, and device fingerprints had yet to play a significant role in risk control processes.
The Development Stage of Gradual Control: Navigating Restriction
As operating systems matured, safeguarding personal data and managing permissions became paramount. System manufacturers started imposing restrictions on data access, making it challenging for developers to acquire original identification data from devices. To overcome these obstacles, third-party manufacturers introduced solutions that involved active collections and comprehensive analysis of device information. This led to the emergence of purpose-built device fingerprint toolkits that required integration into applications. These toolkits considered multiple stability and uniqueness indicators, resulting in enhanced overall stability and effectiveness in risk control measures.
The Stable Stage of Strict Supervision: Adapting to Stringent Regulations
In recent years, regulations and limitations on user data collection have become increasingly stringent. These developments have raised concerns among application developers about potential privacy breaches. Consequently, device fingerprint products based on active data collection have faced scrutiny, prompting developers to consider their removal to mitigate risks. In response, TrustDecision has emerged as a pioneering device fingerprinting solution, designed to navigate these challenges effectively. This includes gathering network information, ja3 fingerprint data, and system image information. Leveraging advanced techniques such as information entropy optimization, comprehensive modeling, similarity matching, and historical index correlation, manufacturers have significantly enhanced device restoration accuracy with our solution. These sophisticated algorithms allow TrustDecision to reconstruct a device's unique identifier with remarkable precision, even in the face of changing device states.
Moreover, TrustDecision's optimized device ID generation process minimizes collision rates between different instances. By leveraging the Snowflake algorithm and optimizing it for high concurrency, we ensure the generation of device IDs that are globally unique, eliminating the possibility of duplicate or shared identifiers. This robust identification process provides a reliable foundation for risk control and enables seamless integration into various business scenarios.
The Future: Technological Breakthroughs for Better User Experience, Higher Security, and Stronger Applicability
Device fingerprinting is undergoing a transformative phase, driven by advancements in technology. This progress promises a future where device identification not only offers better user experiences but also enhances security measures and expands its applicability across various industries. In this evolving landscape, solutions like TrustDecision are at the forefront, recognizing the need for ongoing innovation and adaptation to meet the changing demands.
From the perspective of business form, solutions prioritize achieving a low collision rate and strong restoration ability. Low collision rates can be handled by mature solutions based on open-source discrete algorithms. However, ensuring strong restoration ability is a complex challenge that requires precise matching of indicators and comprehensive data analysis. This process demands the integration of different technical solutions.
Looking toward long-term evolution, the effectiveness of combining active and passive data analysis to find more meaningful and similar relationships is recognized by many solutions, including TrustDecvice. This approach offers several distinct advantages:
- Safety and Compliance: Prioritizing safety and compliance ensures that device fingerprint solutions are widely accepted by customers and the market. By emphasizing data protection and privacy, solutions like TrustDevice, aligning with regulatory requirements, can gain trust across different industries.
- Enhanced Customer Experience: By minimizing the need for user authorization, solutions can offer a seamless and user-friendly experience. Application developers will find it easier to integrate these solutions, resulting in smoother user journeys and increased adoption rates.
- Long-Term Self-Evolution: Device fingerprint solutions like TrustDevive can possess the inherent ability to adapt and evolve over time, effectively confronting new challenges and staying at the forefront of risk control measures, ensuring ongoing effectiveness.
Moreover, the reliance on actively collected data in traditional device fingerprints has been reduced. The focus has shifted to passive attribute acquisition, resulting in improved user experiences, enhanced security, and broader applicability. By reducing the complexity of data processing and analysis, this kind of solutions offer better user experiences and increased security while maintaining their effectiveness.
As technological breakthroughs continue to occur, there is potential for the emergence of simpler and safer solutions that no longer rely on complex data processing technologies. This signifies a moment when device fingerprints transition from being a historical necessity to fulfilling the dreams of application developers. With advancements in basic science, device fingerprinting will continue to offer better user experiences, higher security, and stronger applicability in the future.
In conclusion, the future of device fingerprinting lies in technological breakthroughs that prioritize user experience, security, and applicability. By combining active and passive data analysis, device fingerprint manufacturers can achieve low collision rates and strong restoration abilities. These advancements, including the emphasis on safety, compliance, and long-term self-evolution, pave the way for a future where device fingerprints become simpler, safer, and more effective in meeting the needs of application developers and users alike.






.jpeg)
.jpeg)
.jpeg)





