1. What is payment fraud and its impact
Payment fraud is a way for cyber criminals to deprive victims of their money, personal property and other benefits through any type of false or illegal transactions. In daily Internet online transactions, it mainly involves the process of selling and realizing stolen goods after making payments for physical or virtual products through e-commerce, gaming, social networking, and other websites containing transaction attributes due to the theft of personal information such as bank cards and valuable accounts.
Payment fraud generally has the 3 characteristics in the following:
1) Payment fraud primarily arises from unauthorized transactions.
2) It is often accompanied by bulk spam registration, account theft and card skimming.
3) Fraud generates a lag in chargeback notifications, especially for bank card chargeback, often with a lag period of 1-3 months or more.
Based on the above-mentioned factors, payment fraud has the characteristics of high difficulty in prevention and control, long affecting time, and long lasting process of fighting and preventing.
Impact of payment fraud:
If payment fraud is not effectively prevented and controlled, the most immediate impact is the potential for large fraud and capital loss to business development. In addition, especially for card payment fraud, if the chargeback index is exceeded, there will also be fines from the card organizations and even the risk of termination of cooperation with the payment channel.
And the actual impact of payment fraud is far greater than the loss of fraudulent funds and related fines and penalties. More importantly, it leads to secondary waste caused to the business's own operating costs, marketing expenses, and even to the brand reputation.
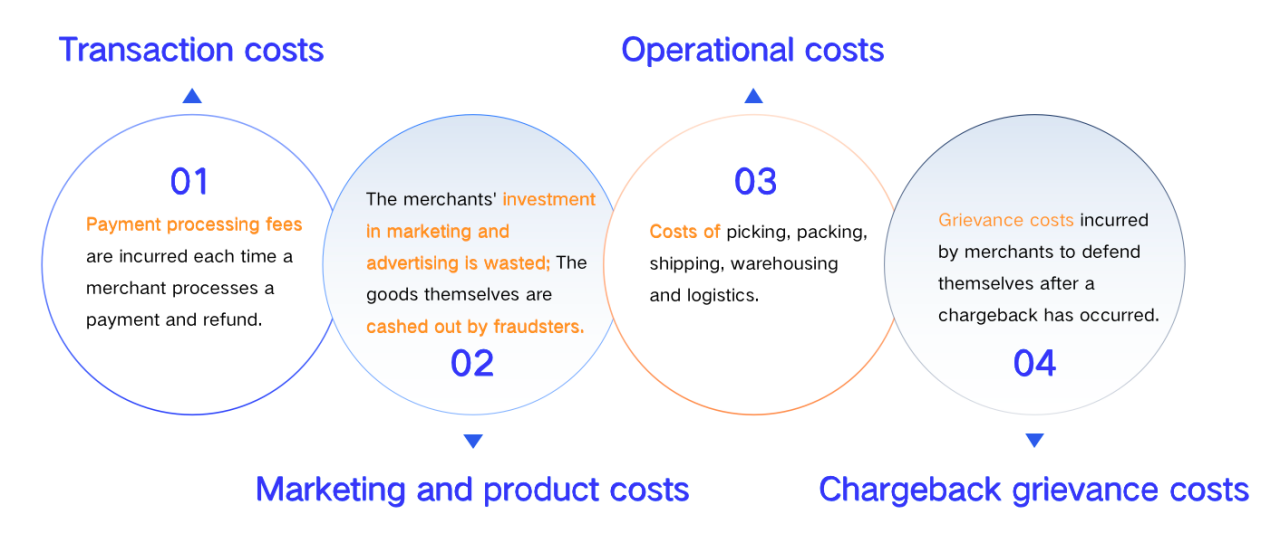
2. Risk characteristics of payment fraud
Payment fraud gangs tend to have the following transaction characteristics in order to conceal their bulk operations.
1) Register a large number of spam accounts and hide identity information.
2) Deliberately modify the actual delivery address or perform ambiguous processing to circumvent the behavior of continuously using the same delivery address.
3) Conduct bulk payment attempts with different bank cards through manual or scripted operations to confirm the availability of counterfeit bank card materials.
In terms of fraud prevention and control, the commonly used associated media are email, cell phone number, delivery address, bank card, device fingerprint, and IP; of which the first 5 are strongly associated media, and IP belongs to the weakly associated media. The above transaction characteristics, the fraud costs are very low in registering bulk accounts (email, cell phone), modifying delivery address, and conducting bulk payment attempts with different bank cards. Fraudsters also often constantly change to hide the crime through such methods. Therefore, the core of how to string together the fraud characteristics lies in the requirement of having unique identification capability of device fingerprints.
Through the device fingerprint as the core correlation medium, fraudsters can be effectively associated, thereby forming a targeted prevention and control program.
3. Specific case and value of prevention and control
A cross-border e-commerce platform suffered a large-scale payment fraud attack:
In June 2022, an e-commerce platform suffered a large-scale payment fraud attack in which fraudsters kept buying large-value, easy-to-sell products by frequently registering spam accounts and attempting to pay with a large number of counterfeit bank cards. It resulted in the usual number of payment requests of about 6,000 or so per day reaching more than double the previous number after the fraud attack, with the overall fraud rate rising to about 1%. In total, over $100,000 in fraudulent funds were lost over a one-month period, moreover, regulatory correction warnings and fines were also issued and received from card organizations.
In this case, by strengthening the intervention of risk control, using device fingerprint as a key medium for fraud ring identification, backtracking groups so as to form links, portraying risk group portraits, and conducting in-depth fraud ring correlation analysis, targeted transaction blocking can be formed for such bulk fraud attacks that have obvious aggregation and coordinated nature.
Prevention and control value: After about 3 weeks of continuous attack and prevention, this fraud ring was effectively controlled, and the overall fraud rate was reduced to less than 0.3%, with a reduction of 70%, recovering fraudulent capital losses of about $70,000 per month. Meanwhile, through accurate fraud interception, the disturbance to normal users was reduced, and the overall payment success rate was increased by 3%, and the GMV growth of about $200,000 per month was indirectly increased.
4. Device Fingerprint application methods
Application method 1: Abnormality detection - core correlation medium of transaction information

The above figure shows the schematic diagram of some transactions of the fraud ring: From the figure, it can be intuitively seen that in 5 fraudulent transactions, the fraudster deliberately keeps changing the registered email and cell phone number, and tries to modify the device information and hide the crime path. However, based on device fingerprints, seemingly unrelated transactions can be effectively correlated to form an orderly link relationship and targeted classification of high-risk fraudster groups, thus, the tagging monitoring and prevention of fraudulent groups is targeted.
Application method 2: Group portrait construction - key pivot points of complex networks in Knowledge Graph
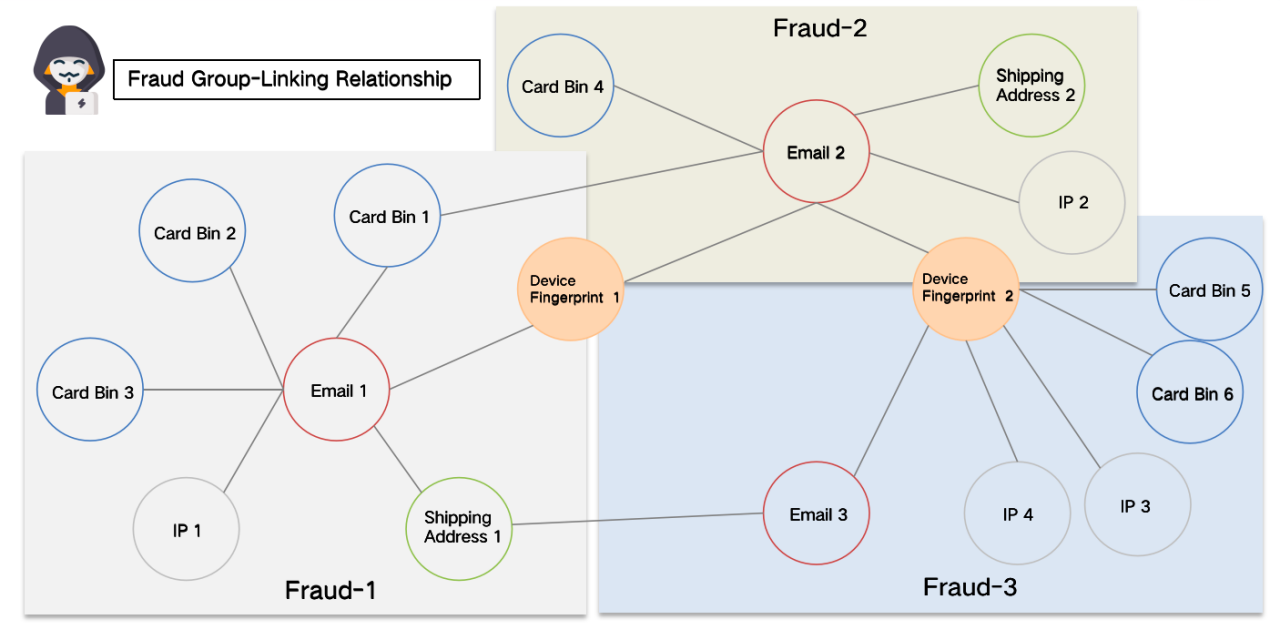
Based on the construction of Knowledge Graph, the association relationship of key nodes in the transaction network is extracted, and a variety of supervised and unsupervised fraud ring models can be developed through graph data mining, change trends of dynamic network clusters, and paths computational analysis, etc. in combination with machine learning algorithms. In the complex and changing crime chain, it can continuously portray the risk groups and identify the clustering groups more accurately and effectively.
5. Conclusion
As the most critical information medium in identifying payment fraud, device fingerprint plays a core identification role for risk trend monitoring, user information association, abnormal risk characteristics detection, and group portrait portrayal. In the payment fraud scenario, no matter how other transaction information is hidden and changed, device fingerprint, as the most solid identification tool for fraudsters work, will effectively play a key supporting role in the long run.






.jpeg)
.jpeg)
.jpeg)





