Generative AI is shaking up content creation and data processing—but it’s also bring massive new challenges for online identity verification. Advances in deepfake technology, in particular, have become a serious hurdle for financial identity systems. With hyper-realistic text, images, and audio, spotting fake content is harder than ever, even for trained detection models.
In countries like Indonesia, Mexico, and the Philippines, financial institutions face even more hurdles: a lack of unified, reliable data sources for verifying identities, low bank card adoption, weak real-name verification services, and sketchy verification for e-wallets and other payment platforms. All this creates the perfect storm, making identity verification and fraud prevention a lot riskier and harder to manage.
Social engineering tactics are also evolving. Attackers impersonate government agencies or financial institutions, luring victims into sharing screens or SMS codes. Mass-distributed fake app links promising loans or prizes exploit human nature—trust, curiosity, or the appeal of a deal—to steal personal data. These attacks don’t just harm individuals; they also affect platform security and reputation.
With social engineering, generative AI, and attacking softwares constantly advancing, the pressure is on financial institutions to protect their core assets. These risks extend beyond identity verification, impacting transaction security, data protection, and anti-fraud measures. Strengthening end-to-end risk management has become essential for staying ahead in this rapidly evolving landscape.
Common Traps and Data Theft Tactics in the AI Attack Chain

By capitalizing on weaknesses in online security and user behaviors, attackers exploit AI to automate and amplify fraudulent activities. Understanding the most common traps and theft methods helps institutions better prepare and defend against these escalating risks.
1. Gathering Identity Data
Attackers start by collecting the target's personal information through various methods. This could involve social engineering tactics to trick victims into revealing personal details or exploiting data exposed in previous breaches. With this info in hand, they can pose as the victim to apply for loans, access accounts, or even swipe assets—all without raising a red flag.
2. Initiating Applications and Account Changes
Once attackers have obtained the necessary identity data, they move to submit fake applications to secure credit or initiate account change processes, such as updating linked phone numbers, bank accounts, or payment passwords. These changes give attackers control over the victim’s accounts, often carried out late at night to delay detection by the victim.
3. Withdrawing and Transferring Funds
Finally, attackers withdraw funds or credit from the victim's accounts. This might include direct transfers, online purchases, cash withdrawals, or other forms of fund movement. In some cases, funds are quickly bounced across multiple accounts to evade tracking and make recovery more difficult.
In these scenarios, even with safeguards like biometric checks, SMS codes, and passwords, those “ironclad” protections can still fall short. Attackers are constantly finding clever ways to sidestep them, turning trusted defenses into mere speed bumps in their schemes.
The Blind Spots in Risk Management
Even the best risk management strategies can overlook key vulnerabilities, leaving openings for fraudsters to exploit. For example, when businesses focus too heavily on areas like credit approval while overlooking broader verification and security measures, they risk leaving accounts exposed. Identifying and addressing these blind spots can make all the difference in protecting core assets. Here’re some of the most common blind spots that we discovered throughout our anti-fraud practice with financial clients.
Over-Focusing on Credit Approval
Credit risk decisioning is key to securing transactions and stopping fraud in its tracks. But some institutions are so laser-focused on the credit approval stage that they’re missing the bigger picture—overlooking crucial checks like verifying account ownership and securing sensitive actions. These blind spots leave the door wide open for account takeovers, asset theft, and reputation hits.
In this case, building a full-spectrum risk management system means looking beyond credit checks. Financial institutions need to give equal weight to validating account ownership to prevent account takeover, scanning for risky actions for all time, setting up trusted verification frameworks, fostering cross-departmental collaboration between risk, IT, compliance, and operations, and educating their customers on account safety practices.
Over-Reliance on Single Verification Methods
Relying on just one form of verification — like passwords, security questions, or only triggering facial recognition for certain actions — is a risky bet. Once these defenses are compromised, there’s often nothing left to back it up. This over-reliance on “one-and-done” verification is an open invitation for attackers, who can easily bypass weak defenses through social engineering or tech hacks, bringing the entire system crashing down.
Missing Strategies for Key Business Scenarios
Risk management strategies for critical business scenarios are the backbone of account security and fraud prevention, as well as a vital part of post-incident review. It’s recommended that product teams assess the risk levels and frequency of these scenarios, designing user-friendly interfaces that can also capture necessary risk data. Meanwhile, risk and development teams should create backend verification strategies to match.
Without effective safeguards for high-risk actions — such as large transactions, account updates, or credential changes — even the best anti-takeover strategies fall short. Attackers are quick to spot these gaps, using them to mimic legitimate users and conduct unauthorized actions, slipping right past outdated defenses.
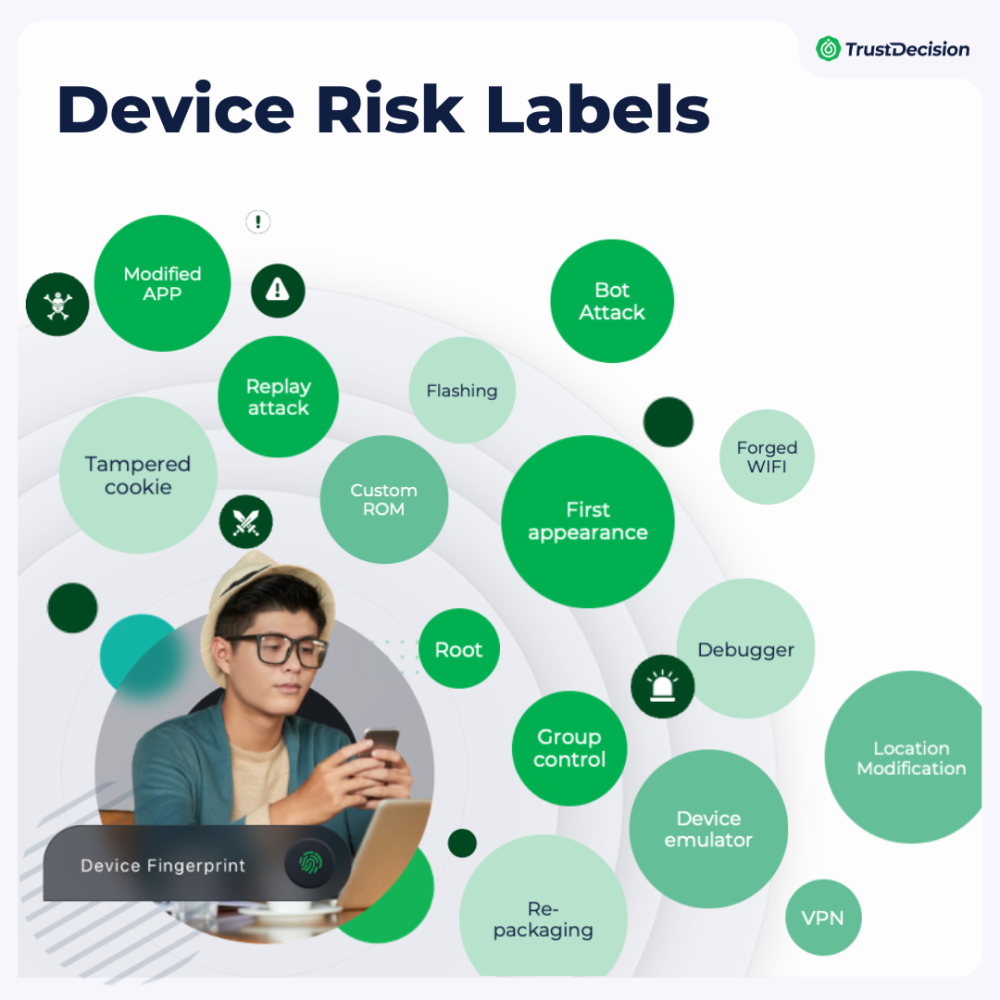
Underutilization of Mobile Device Fingerprinting
Device fingerprinting assigns a unique identifier to each device based on various data points, enabling risk assessment for app operations. Yet, many financial institutions are barely scratching the surface with this tech, leading to a lack of critical behavioral and environmental insights for key transactions. This gap makes it difficult for platforms to detect and prevent abnormal behaviors like bot attacks, emulators, and injection attacks, increasing the risk of fraud.
Building Up Comprehensive Solutions for Financial Security
To respond to these evolving threats, financial security needs to be comprehensive. By combining proactive monitoring, robust verification, and fully leveraging device risk detection, institutions can protect user accounts, fortify data integrity, and build trust across all fronts.
End-to-End Risk Monitoring and Alert
To fully protect core assets like account security, it’s essential to establish a monitoring and alert system that covers the complete user journey such as registration, login, authentication, credit approval, usage, and personal information updates. This involves tracking key indicators, like unusual activity, multiple failed login attempts, logins from unfamiliar devices or locations, and sudden changes in account settings. In response, measures like downgrading access, freezing accounts, or blocking actions can be applied to ensure security.
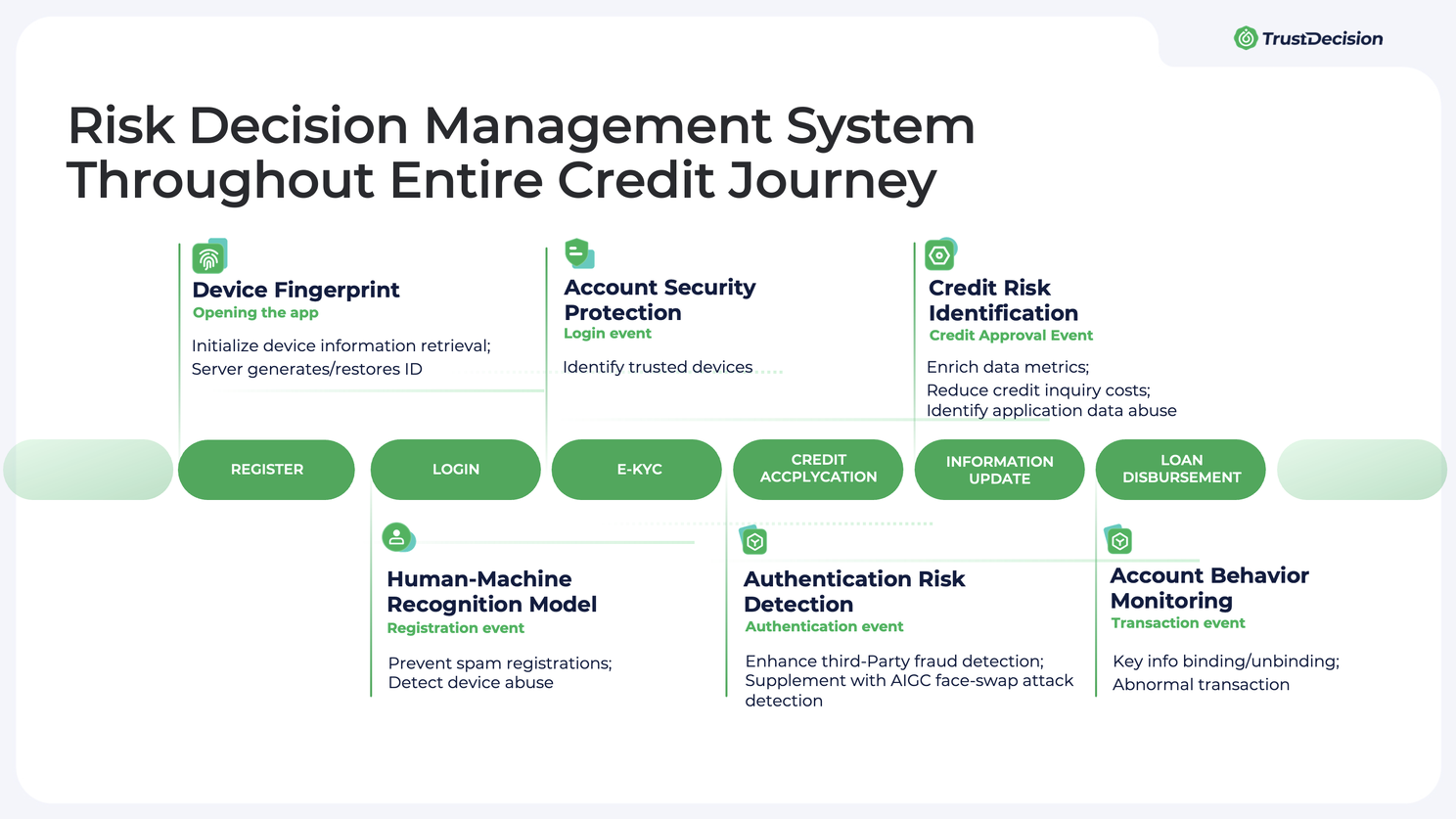
Device Fraud Detection
Effective device-relating fraud detection needs continuous technology upgrade and risk tools identification.
TrustDecision has developed an advanced anti-fraud system, covering device risk perception, risk identification, risk handling, and fraud ring detection, strengthening defenses against telecom and network fraud. Our real-time monitoring can spot over 3,000 attacking softwares, over 20 risk tools, and over 100 risk labels, including VPNs, emulators, group control, fake locations, jailbroken devices, and screen-sharing hacks, updating every week to stay ahead of the evolving threats.
Cross-Referencing Self-Reported Data with Reliable Sources
Active verification of user profiles goes beyond simple cross-checking of self-reported data. OCR processes, liveness detection, and new phone numbers — being user-reported elements — pose manipulation risks. To counter this, cross-referencing the self-ported data with authoritative datasource is necessary. For example, matching ID number with phone number, ID number with name, bank account with ID number, bank account with name, and facial image with official records. Strengthening these pairs with additional verification helps reinforce the account security system and builds a more accurate identity profile for each customer.
Data Modeling of Key Indicators
A robust data model analyzing key indicators should include establishing baseline for approved login data, profiling user behaviors for anomalies, and enabling Multi-Factor Authentication (MFA).
1. Firstly, the system digs into users’ regular login habits — analyzing login times, locations, devices, and network conditions. By establishing a baseline for a normal login, it becomes easier to catch login patterns that deviate sharply, so unauthorized access can be flagged and shut down quickly.
2. A risk persona is created from a user’s historical behaviors and transaction patterns to detect fraud by continuously monitoring these activities - if the model detects sudden changes that deviate from past behavior, it may indicate an attempted fraud. For example, sudden activity in a new country could indicate account compromise. Learn more about Global Risk Persona.
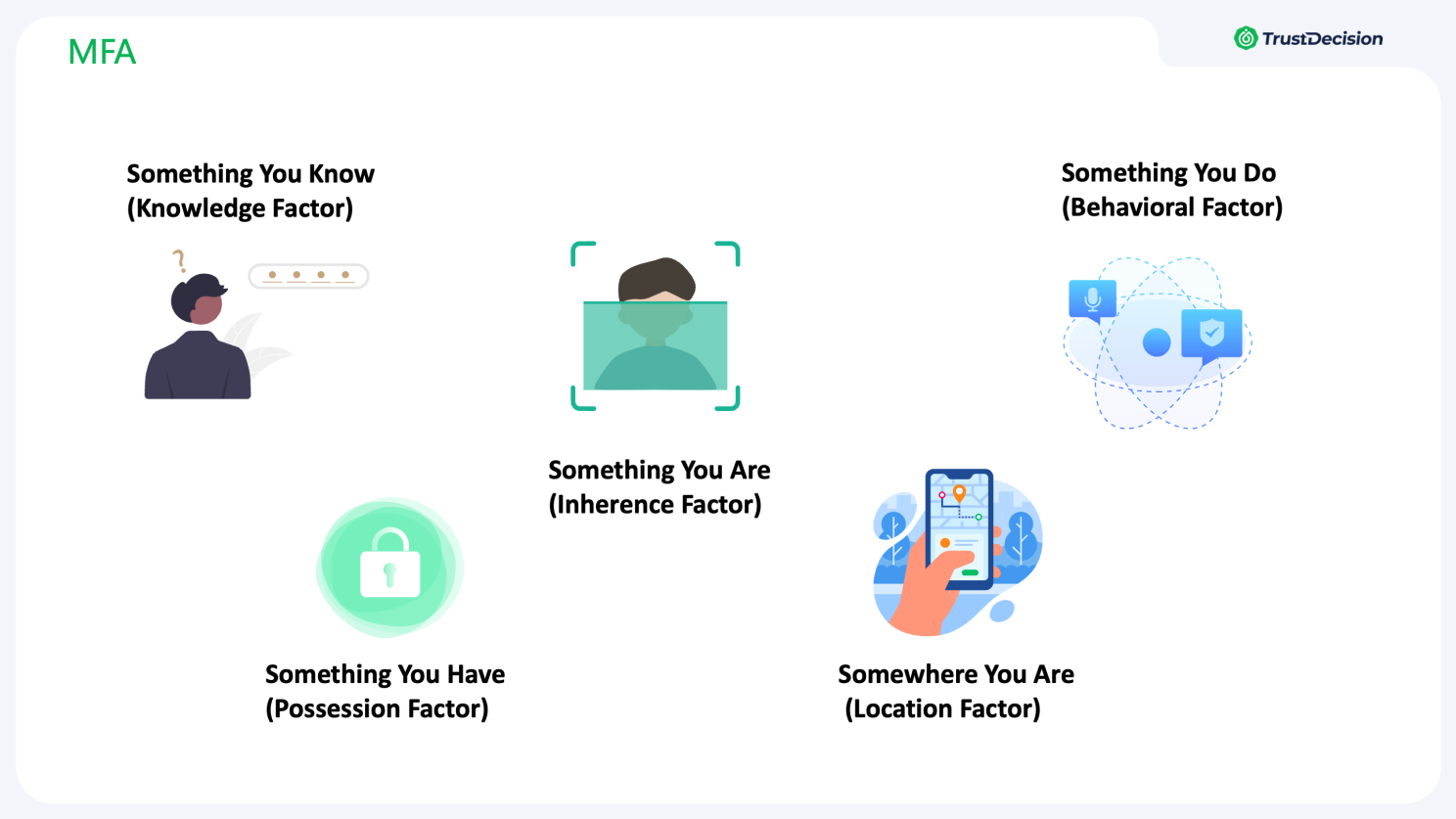
3. MFA adds an additional layer of account security even if one factor is compromised. MFA includes knowledge factors (passwords, PINs, or security questions), possession factors (smart cards, tokens, SMS codes), and inherent factors (biometrics like fingerprint, facial recognition, or iris scans). Successful MFA shouldn’t rely on just one factor; instead, it needs to smartly combine these based on the specific risk scenario and transaction type. Real-time context should shape the mix, using data like user behavior, location, and device fingerprinting to dynamically adjust authentication requirements, creating a strong safety net for users.
In sum, as AI-driven threats grow more sophisticated, financial institutions must embrace a proactive, multi-layered approach to security. From deepfakes to social engineering, attackers exploit gaps traditional defenses may overlook. Comprehensive risk management strategies—including tools like TrustDecision’s Global Risk Persona—help institutions protect user accounts, secure data, and sustain customer trust. Strengthening these defenses is crucial to staying ahead of evolving threats and building a resilient security framework for the future.
About TrustDecision
TrustDecision is a global leader in risk management and fraud prevention solutions, empowering businesses with solutions to safeguard digital identities, secure transactions, and enhance customer trust. Leveraging our strong data modeling capability and actionable insights, TrustDecision enable financial institutions to detect and mitigate fraud threats in real time, and partners with clients worldwide to build resilient security frameworks.








.jpeg)




