We might think of things that are asleep as less harmful and more vulnerable—like a sleeping leopard, a dormant volcano, or even Sleeping Beauty, if you will. But that’s not entirely true. Things that seem asleep may actually be dormant for now, lying in wait for the perfect moment to strike with a coup de grâce. That’s what we’re gonna talk about in this article: the lurking threat in your lending platform — sleeper fraud.
What is Sleeper Fraud?
Sleeper fraud is a type of financial fraud where a fraudster (or fraud gangs) opens or takes over an account — often a credit card or bank account — and lets it “sleep” for weeks or months without raising red flags, mimicking the behavior of an idea users. Once the account has built trust or reached a favorable status, the fraudster suddenly “wakes it up” with a burst of fraudulent activity such as a large cash-out, and vanish. Instead of really falling asleep, they’re just playing the long game.
That being said, compared with instant default or identity theft, the seemingly normal behaviors of sleeping fraudsters makes them harder to detect by traditional rule-based fraud flagging system. At first, they play by rules: borrowing small amount, repaying on time for 2–3 loan cycles, and slowly moving to larger loans. Additionally, traditional systems often look at short-term behavior (like past 7 or 30 days), while sleeper fraud spans longer period like weeks or months.

In addition to this elusive nature, what else also makes sleeper fraud so dangerous?
One key factor is the fragmented nature of today’s digital lending ecosystem. With dozens or even hundreds of platforms operating independently, there’s often limited sharing of borrower data or fraud intelligence. This allows fraudsters to exploit the gaps—defaulting on one app while maintaining a clean record on another. Without cross-platform visibility, it becomes difficult to piece together suspicious borrowing patterns or detect coordinated attacks.
At the same time, advances in generative AI and ongoing cybersecurity vulnerabilities have made it easier than ever to create and manage fake accounts. Fraudsters can now generate realistic-looking documents, bypass facial recognition with deepfakes, and rotate through low-cost devices or SIM cards. This gives them the tools to operate networks of sleeper accounts at scale, while staying under the radar of basic verification systems.
Many sleeper fraudsters also target thin-file users—borrowers with little or no formal credit history—because they follow a predictable onboarding path. Lenders typically offer small initial loans and rely on early repayment behavior to gauge creditworthiness. Fraudsters exploit this by repaying a few early loans to build trust, only to default once higher loan limits are unlocked. Over time, this erodes confidence in the thin-file segment, making it harder for genuine borrowers to access fair credit.
Is Sleeper Fraud a Dead End for Businesses?
Facing this type of fraud can be incredibly frustrating—but every action leaves a trail. Here are some clues to watch out for when monitoring your lending business.
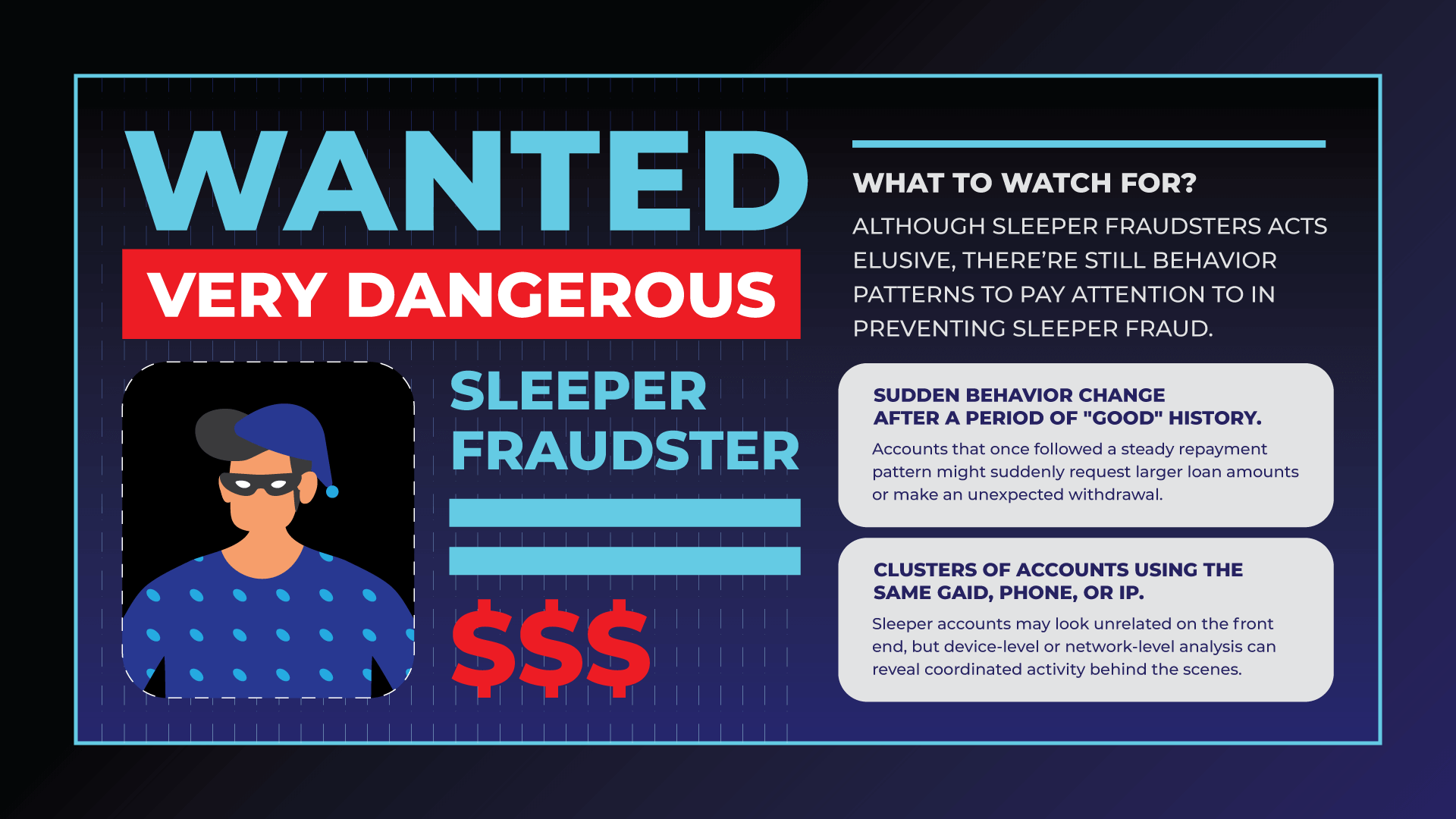
1. Watch for any sudden behavior change after a period of "good" history.
One of the most telling signs is a sudden shift in borrower behavior. Accounts that once followed a steady repayment pattern might suddenly request larger loan amounts or make an unexpected withdrawal. On its own, this could seem like natural credit progression—but combined with other signs, it could indicate a fraudster preparing to cash out.
2. Clusters of accounts using the same GAID, phone, or IP.
Another key indicator is the presence of shared or recycled digital environments. Fraud rings often reuse the same devices, GAIDs, phone numbers, or IP addresses across multiple accounts. These sleeper accounts may look unrelated on the front end, but device-level or network-level analysis can reveal coordinated activity behind the scenes.
These patterns are often difficult to detect with traditional tools, especially when fraudsters carefully mimic the behavior of trustworthy users. That’s why smart lenders are turning to device fingerprinting and behavioral analytics to connect the dots—tracking borrowing patterns over time and across platforms, rather than evaluating each action in isolation.
In more advanced setups, lenders are also building network-based fraud models and participating in shared intelligence ecosystems. This allows them to flag suspicious accounts faster, even if the fraud is still in its “sleeping” stage.
In a Nutshell
Not everything that lies dormant is harmless. Just like a volcano that erupts after years of silence, sleeper fraud doesn’t show its true face until the damage is done. But that doesn’t mean lenders are powerless.
With smarter detection methods—like device intelligence, behavior monitoring, and cross-platform pattern analysis—you can spot the warning signs long before the blow-up. Solutions like Application Fraud Detection are designed to help businesses manage threats such as sleeper fraud, fake or synthetic identities, and other types of application fraud—allowing digital lending platforms to focus more on growth and less on struggling with fraud attacks.
The fraud may be sleeping, but your system doesn’t have to be.






.png)






