As the digital landscape continues to evolve, businesses face increasing challenges in fraud prevention and user protection. Device fingerprinting has emerged as a powerful technique to combat fraud and enhance cybersecurity. While developing a device fingerprinting system in-house may seem daunting, TrustDevice offers comprehensive solutions that help you with the process. In this article, we will explore the complexities involved in generating device fingerprints in-house, highlight the challenges, and demonstrate how TrustDevice can empower your business.
How to develop Device Fingerprint In-house?
Developing a robust device fingerprinting system in-house requires a systematic approach and the right resources. Here's an exhaustive guide to help you navigate the process:
Step 1: Define Objectives and Use Cases
Start by clearly defining your objectives and use cases for device fingerprinting. Determine the specific purposes for which you need device fingerprints, such as fraud detection, authentication, or personalized user experiences. This will help you tailor your solution to meet your specific requirements and guide your decision-making throughout the development process.
Step 2: Research Existing Solutions
Before diving into development, conduct thorough research on existing device fingerprinting solutions and technologies. Explore open-source libraries, frameworks, and APIs that can provide a foundation for your system. Evaluate their features, compatibility, and community support to determine which options align best with your needs. Leveraging existing solutions can significantly reduce development time and costs. You may explore open-source solutions like FingerprintJS, OpenAmsterdam, or TrustDevice's Fingerprinting Library for assistance in implementing device fingerprinting.
Step 3: Gather Necessary Resources
Developing a device fingerprinting system requires a range of resources. Ensure that you have access to skilled developers, data scientists, and cybersecurity experts who can contribute to different aspects of the project. Additionally, allocate appropriate hardware and software resources, including servers, databases, and development tools, to support the implementation and ongoing maintenance of your solution.
Step 4: Data Collection and Feature Selection
Identify the data points you need to collect for generating device fingerprints. This may include device attributes (e.g., operating system, screen resolution), network information, browser details, sensor data, and behavioral patterns. JavaScript, SDKs (such as iOS or Android), or server-side code all can be used for data collection. Determine which features are most relevant and effective for your use cases. Carefully design the data collection process to ensure transparency and compliance with privacy regulations, obtain user consent, and protect sensitive information.
Step 5: Develop Data Processing and Analysis Pipeline
Implement a data processing pipeline to handle the collected device data. This pipeline should include modules for data cleaning, feature extraction, and data transformation. Apply appropriate algorithms and statistical techniques to analyze the collected data and derive meaningful insights. Machine learning approaches, such as clustering or classification algorithms, can be employed to identify patterns and generate device fingerprints.
Step 6: Implement Security Measures
Ensure that your device fingerprinting system incorporates robust security measures. Implement encryption protocols to protect sensitive data during transmission and storage. Apply hashing or tokenization techniques to anonymize personally identifiable information (PII) and maintain user privacy. Regularly update and patch your system to address security vulnerabilities and stay ahead of evolving threats.
Step 7: Building a Secure Device Fingerprint Database
Create a centralized and secure database to store device fingerprints or hashes. It should be designed to efficiently handle large volumes of data and provide fast retrieval capabilities for real-time fraud detection and user authentication.
What are the difficulties and challenges of in-house development?
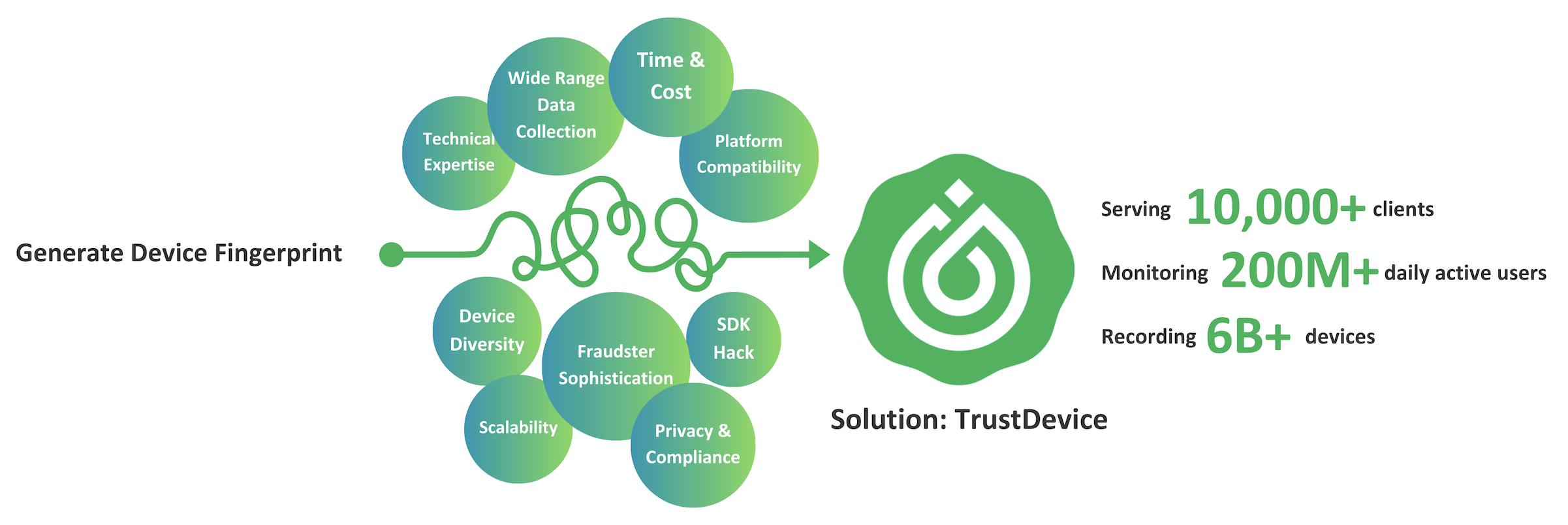
While generating device fingerprints in-house offers advantages in terms of customization and control, it's crucial to be aware of the challenges involved. Developing an in-house device fingerprinting solution requires expertise, resources, and a thorough understanding of the complexities involved. Here are some key difficulties you may encounter when embarking on the journey of developing device fingerprints in-house:
Technical Expertise
Developing an effective device fingerprinting system demands a deep understanding of various technologies, including device identification, data collection, signal processing, and pattern recognition. It requires expertise in programming languages, data analysis, machine learning, and cybersecurity. Acquiring and maintaining a team with such diverse skill sets can be a significant challenge, especially for smaller organizations or those without dedicated resources.
Data Collection and Interpretation
Accurately collecting and interpreting device data is critical for generating reliable device fingerprints. It involves capturing a wide range of parameters, such as device identifiers, network information, sensor data, and behavioral patterns. Ensuring the accuracy and consistency of this data across different devices and platforms can be complex and time-consuming. Additionally, the interpretation of this data requires advanced algorithms and statistical models to extract meaningful insights and generate unique device fingerprints.
Device Diversity and Platform Compatibility
The vast landscape of devices, operating systems, and platforms poses a significant challenge in generating comprehensive device fingerprints. The proliferation of smartphones, tablets, IoT devices, and various web browsers requires extensive testing and compatibility checks to ensure the accuracy and coverage of device fingerprints across diverse environments. Developing and maintaining a solution that adapts to the ever-evolving device landscape can be resource-intensive and demanding.
Fraudster Sophistication and SDK Hack
Fraudsters are continuously evolving their techniques to bypass security measures, including device fingerprinting. They employ advanced methods such as device emulation, IP spoofing, and VPNs to obfuscate their true identity and mimic legitimate user behaviors. Developing an in-house device fingerprinting solution that can effectively detect and mitigate these sophisticated attacks requires ongoing research, updates, and countermeasures to stay ahead of fraudsters.
Fraudsters also relentlessly seek opportunities to exploit weaknesses in software development kits (SDKs) employed for device fingerprinting to produce false or inconsistent device IDs. By examining the SDK code, they can identify patterns that indicate legitimate user behavior and replicate those patterns in their fraudulent endeavors. Some fraudsters go as far as using reverse engineering techniques to gain insight into the inner workings and vulnerabilities of the SDKs. To confront these challenges effectively, it is vital to implement protective measures such as code obfuscation, encryption, regular updates, continuous monitoring, and collaboration with the security community.
Scalability and Performance
Handling a large volume of device data and processing it in real time can pose scalability and performance challenges. Device fingerprinting systems need to be capable of handling high traffic loads without compromising accuracy or response times. Efficient data storage, retrieval, and analysis mechanisms are crucial to ensure the system's scalability and performance.
Privacy and Compliance
Data collection and storage must comply with privacy regulations and prioritize user consent. Implement robust data protection measures, including encryption and access controls, to safeguard collected device data and prevent unauthorized access or breaches.
Time and Cost Considerations
Developing a robust and reliable device fingerprinting system in-house requires significant investment in terms of time, resources, and costs. It involves extensive research, development, testing, and maintenance efforts. The process may require the acquisition of hardware and software licenses, and the allocation of dedicated personnel. Additionally, the opportunity cost of diverting resources from core business activities should be carefully evaluated.
How can TrustDevice help you?
TrustDevice, developed by TrustDecision, offers a comprehensive, end-to-end solution for generating device fingerprints. Rather than simply simplifying the process, TrustDevice provides the entire process as a Software as a Service (SaaS), enabling businesses to effortlessly incorporate device fingerprinting into their fraud prevention and cybersecurity strategies. Let's delve into how TrustDevice addresses the challenges mentioned above and provides a seamless experience for businesses:
Wide Coverage and Streamlined Integration
TrustDevice boasts comprehensive coverage across various device types, including Android, iOS, Web, H5, and applets. This extensive coverage ensures that businesses can effectively capture device data across different platforms, enhancing the accuracy and reliability of their device fingerprints.
Stability and Reliability
With a track record of serving over 10,000 clients and 6 billion+ devices, TrustDevice delivers stable and reliable performance. It boasts a fingerprint accuracy rate exceeding 99.9% and provides an extensive array of risk labels for effective fraud detection.
Unparalleled Safety and Advanced Technologies TrustDevice leverages cutting-edge technologies to ensure unparalleled safety in device fingerprinting. It employs code virtualization and obfuscation techniques, making it extremely challenging for fraudsters to reverse-engineer and manipulate device fingerprints. By incorporating advanced security measures, TrustDevice minimizes the risk of fraudulent activities and strengthens overall cybersecurity.
Core Intellectual Property
TrustDevice is built on fully independent intellectual property rights, underpinned by patented technologies, ensuring uniqueness and cutting-edge capabilities.
Security Compliance
TrustDevice is committed to the highest security and compliance standards. It adheres to GDPR, CCA, PCI DSS, ISO 27701, and ISO 9001, guaranteeing the safety and integrity of your data.
Easy Deployment
TrustDevice offers Software as a Service (SaaS) deployment, reducing integration costs and enabling rapid access to device fingerprinting services. This streamlined approach ensures quick and hassle-free implementation.
Generating device fingerprints in-house presents both challenges and opportunities. By partnering with experts like TrustDevice, businesses can overcome difficulties and enjoy the benefits of customization, control, and enhanced fraud prevention. TrustDevice, with its wide coverage, stability, security compliance, and ease of deployment, empowers businesses to protect their customer journey effectively.
Explore TrustDevice and embark on a journey of advanced device fingerprinting for fraud prevention and personalized user experiences here. Still uncertain about whether TrustDevice is the perfect solution for your needs? Take the next step and schedule a personalized demonstration to gain a deeper understanding of our comprehensive solution. Discover how TrustDevice can be tailored to meet your specific requirements. Don't miss out on the opportunity to explore our offerings in detail.
Where to get support:
For technical support with TrustDevice's open-source library, visit GitHub Issues to submit bugs or Discussions to ask questions. Engaging publicly with the open-source community will benefit others facing similar issues.






.jpeg)
.jpeg)
.jpeg)





