Definition
As a basic tool product, device fingerprint has high business value in multiple scenarios, such as identity verification, transaction fraud, and promotion abuse. Its main function is to create and maintain a globally unique identifier for a physical device within a certain range: the device ID. For a long time, ensuring the device ID's stability has been an important factor in measuring this product's excellence. Among them, the restoration ability and the uniqueness guarantee are the two most important indicators for stability evaluation. Restoration capability mainly refers to whether the device fingerprint can restore the original device ID of the device after the device state is changed. The uniqueness guarantee mainly refers to ensuring the uniqueness of the device identity code, at least within the scope of the system, and different devices are not allowed to share the same device ID.
So how to ensure these two characteristics?
The product of device fingerprint has been jointly maintained by system providers and industry standards for a long time. In the beginning, these supports are transparent, and application developers can easily obtain a relatively stable device identity. With the rapid development of devices, systems, and Internet applications, these supports have gradually become introverted, and application developers have to find other solutions. This process has probably gone through several major stages: the initial stage of opening, the development stage of gradual control, and the stable stage of strict supervision. There are huge differences in the solutions adopted in different stages.
In the early days, the overall environment was relatively open. To meet the network equipment supervision policy, the equipment provider will preset the network access identifier of the equipment, such as IMEI, UUID, physical MAC address, etc., into the system. And because the laws and regulations related to personal privacy protection were not perfect at that time, there was no threshold for obtaining this information. Application developers could easily obtain these identifiers by calling the specified API. These identifiers are preset in the initial system of the device by the device manufacturer and the system provider and are defined according to local or international relevant protocol standards. It is precisely because these identifiers are bound by the official agreement and perform well in terms of uniqueness, and because they are preset inside the system, they are relatively safe and difficult to change when the source code is not disclosed. This device ID preset by the system is sufficient to support the use of most business scenarios, and the cost of obtaining these IDs is very low. But from another perspective, this also clarifies black industry practitioners' purpose. They only need to modify these important indicators to achieve the purpose of changing the device ID. The cost of black production attacks in this period is very low, and device fingerprints are not ready for becoming an important part of the risk control process.
With the gradual maturity of the operating system, the protection of personal data and the control of related permissions are becoming more and more important, and system manufacturers have controlled this part of the data to varying degrees. These controls mainly include adding runtime permissions, null authorization, randomizing key API outputs, etc. At this time, relying on the native capabilities of the system has already encountered obstacles, and considering that users tend to refuse authorization, it is even more difficult to obtain the original identification data of the device. To solve these problems, third-party manufacturers have come up with some solutions. They are good at calculating device IDs through the active collection and comprehensive analysis. The device fingerprint at this stage will have a very purposeful tool development kit, which requires users to integrate it into their applications. The main purpose of this tool is to collect device information, including device software and hardware information, environmental network information, etc. After collecting these data, some indicators that combine stability and discreteness will be selected, and then the index relationship between indicators and device information will be established in the database. If it is a new device, a device ID is also generated. These device IDs are implemented through some low-collision rate algorithms, such as the snowflake algorithm, to ensure the uniqueness of the device ID. Due to the comprehensive consideration of the multi-dimensional indicators of the device, the device fingerprint of this period has reached a higher level of overall stability and confrontation and has played a great role in the risk control process.
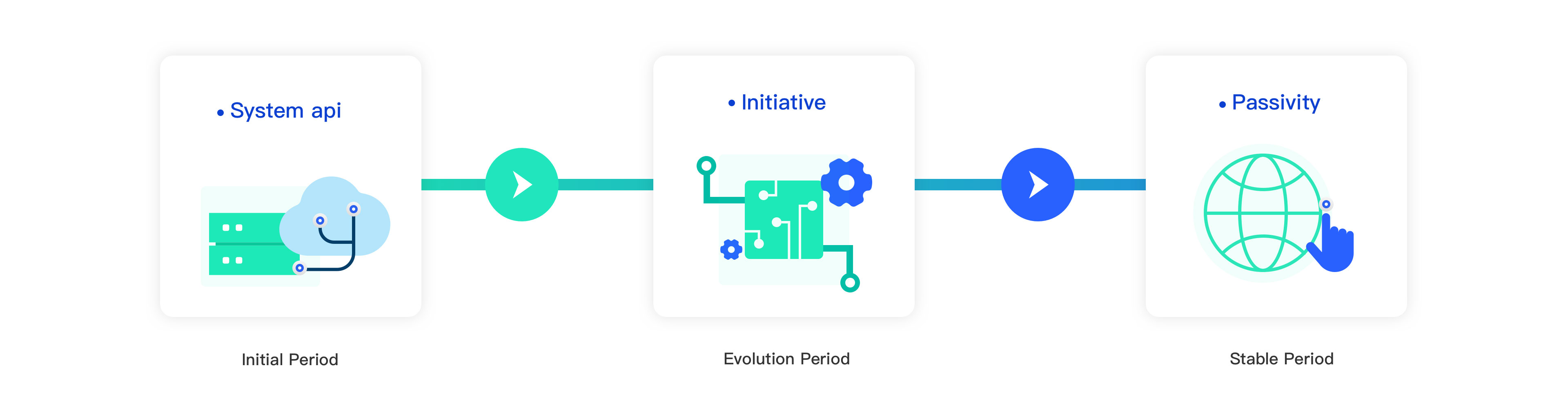
In recent years, whether it is the laws and regulations promulgated by various places or the application market, user data collection has been restricted, involving identity data, device data, behavior data, etc. Now, the collection conditions for these data are extremely harsh, and application developers will be alert to potential violation risks when using actively collected device fingerprint products, and even choose to remove such device fingerprint products when faced with a decision. This is also a common problem faced by device fingerprint manufacturers at present, and it is also a survival problem. Under the huge challenges, companies with deep technology accumulation such as TrustDevice have found key solutions. Based on weakening the active collection of data as much as possible, the collection of passive attributes, such as network information, ja3 fingerprint information, and system image information, has been improved. Based on these data, the equipment is restored with high precision through information entropy optimization, comprehensive modeling, similarity matching, and historical index correlation. At the same time, the device ID generation has also been improved, and the Snowflake algorithm has been optimized for high concurrency, which greatly reduces the collision rate between different instances.
From the perspective of business form, the current core work of device fingerprint manufacturers is still to ensure a very low collision rate and strong restoration ability. The low collision rate can be handled by some open-source discrete algorithms, or improved based on such algorithms, and the solutions in this part are relatively mature. The strong reduction ability is faced with different challenges in different periods. It must match the indicators before and after the equipment status change with high precision and analyze, classify and attribute all the data that can be obtained. This process is extremely complicated and requires the introduction of different technical solutions.
From the perspective of long-term evolution, the combination of active and passive to find more similar relationships must be the best choice for device fingerprint manufacturers. It has several distinct qualities:
1. Safe and compliant, easier to be accepted by customers and the market
2. Very good customer experience, does not require any authorization, and is easier to be accepted by application developers
3. Possess the ability of long-term self-evolution, and is born with a strong confrontation ability
Because of these characteristics, it has also changed the strong dependence of traditional device fingerprints on actively collected data. More importantly, technological breakthroughs, provide a better user experience, higher security, and stronger applicability. Perhaps, with the breakthrough of basic science, in the future, there will be safer and simpler solutions that will no longer rely on complicated data processing technology. That will be the moment when device fingerprints withdraw from the stage of history, and also the moment when all application developers realize their dreams.






.jpeg)
.jpeg)
.jpeg)





