The use of Electronic Know Your Customer (EKYC) is becoming increasingly popular among businesses for verifying the identities of their customers electronically. The EKYC requirements are no longer just the requirements of Banking and Finance industry. Gaming, Media, Ride Hailing and Online Education all require a Digital customer onboarding and EKYC. However, relying solely on EKYC for digital security is not enough, as it only verifies identity and not intent or behaviour. This means that EKYC cannot prevent identity theft or account takeover, nor does it provide end-to-end encryption or secure communication channels. In addition, EKYC can be circumvented, making it less effective in preventing digital threats. Therefore, it is essential to incorporate additional security measures, such as multi-factor authentication, end-to-end encryption, and secure communication channels, to provide robust protection against digital threats.
Device fingerprint adoption to enhance digital security and EKYC
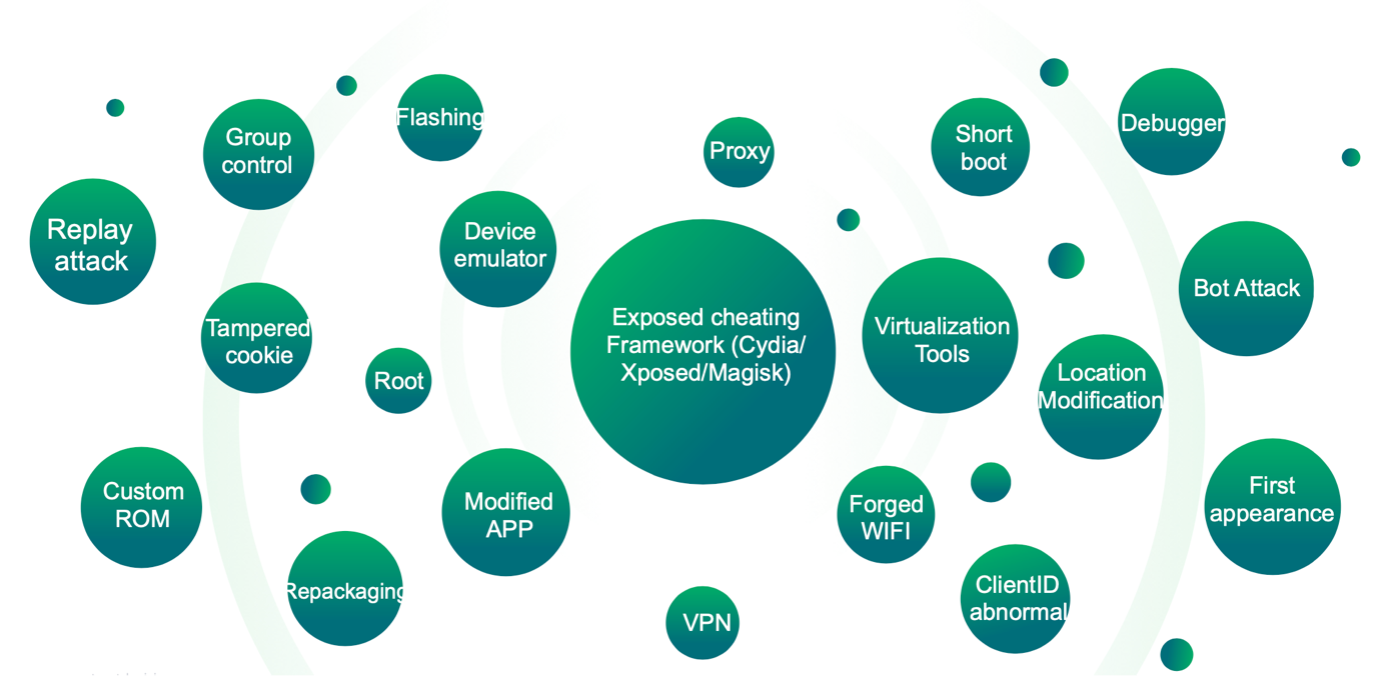
One such security measure is device fingerprinting, which is a technique used to identify and track devices based on their unique characteristics. Device fingerprinting can be used to enhance EKYC by providing additional information about the device being used to access the EKYC service. This technique involves collecting and analyzing data on how a device interacts with a network or system. The data collected is then used to create a unique profile or fingerprint of the device, based on factors such as the device's IP address, operating system, browser type and version, installed plugins and extensions, and other unique characteristics.
By analysing a device's behaviour and comparing it to known patterns of legitimate or fraudulent activity, device behaviour fingerprinting can be used to detect and prevent various types of fraud. These include device fraud, identity fraud, payment fraud, promotion fraud, and fraud ring.
Device fraud refers to the use of a stolen or compromised device, such as a smartphone or computer, to commit fraud. This can include activities such as accessing a victim's financial accounts or using stolen credit card information to make purchases online. Device fraud can occur through various methods, such as phishing scams, malware attacks, and physical theft of a device.
Identity fraud on the other hand, involves the theft or misuse of personal information, such as a person's name, address, Social Security number, or credit card information, to commit fraud. This can include opening new accounts, applying for loans or credit cards, or making unauthorized purchases using the victim's identity. Identity fraud can occur through various methods, such as phishing scams, data breaches, and physical theft of personal documents.
Payment fraud encompasses various illicit activities that involve the exploitation of a payment system to gain unauthorized access to money or goods, including but not limited to credit card fraud, wire transfer fraud, mobile payment fraud, e-commerce fraud, and chargeback fraud. Credit card fraud involves unlawfully utilizing someone else's credit card data to make purchases, while wire transfer fraud entails illicitly transferring money from one account to another. Mobile payment fraud involves fraudulent transactions through mobile payment services, and e-commerce fraud involves using fake credit card or payment data to make online purchases. Chargeback fraud involves customers disputing authentic transactions, leading to merchants losing revenue
Promotion fraud is a form of fraudulent activity in which individuals or syndicates take advantage of promotions, coupons, and discounts offered by e-commerce businesses to make illicit gains. This can involve using fake or stolen promotional codes, creating multiple accounts to use the same promotion more than once, or manipulating codes to increase their value. Promotion fraud can cause serious financial losses to businesses, damage their brand reputation, and reduce customer trust
Fraud ring mining is the process of identifying and disrupting organized groups of criminals who engage in fraudulent activity. To detect fraud rings, businesses and law enforcement agencies typically use advanced data analytics and machine learning techniques to analyse large amounts of data from multiple sources, including financial transactions, customer behaviour, and social media activity. These techniques help identify patterns and anomalies that may indicate fraudulent activity. Some common indicators of fraud ring activity include a high volume of transactions from a single IP address or device, unusual transaction patterns, inconsistent shipping and billing addresses, use of stolen or fake identity information, and links to known fraudulent accounts or activity.
Device fingerprinting can provide valuable information that enhances EKYC, making it a more effective security measure. By combining device fingerprinting with EKYC, businesses can detect and prevent fraud more effectively. For example, by identifying a device's unique characteristics, businesses can verify that the user's device is not compromised or being used by someone else to access the service. This can prevent device fraud and identity fraud. In addition, device fingerprinting can help businesses detect payment fraud by analysing the patterns of payment transactions and identifying anomalies that may indicate fraudulent activity. Finally, device fingerprinting can also help businesses detect promotion fraud by analysing the patterns of promotional code usage and identifying patterns that may indicate fraudulent activity.
A persistent Device ID solution is now a necessary arsenal in Digital Fraud mitigation toolkit and allows to secure customer experience, meet various compliance needs and better protect brand.









.jpeg)




