This article is a collaboration between TrustDecision and IPLL.
Here’s a case: One evening, the risk management team at a leading internet company received an urgent alert: within just ten minutes, a single user account had attempted to log in from three different countries, all far from the account's usual activity zone in Shanghai, China.
This sudden, unusual pattern of cross-border logins immediately triggered the company’s security systems. The risk team quickly dove into the details, analyzing key data points such as IP addresses, device information, and timestamps. Their thorough analysis revealed that these were not normal login attempts. Instead, they were highly suspicious, possibly fraudulent activities. In this scenario, IP addresses became vital clues in tracking down the source of the anomaly.
The investigation showed that two of the IP addresses were linked to a data center in Europe, while the third was from a data center in North America. These logins did not come from the account holder’s usual location but were instead concealed using VPN or proxy services. Acting on this insight, the risk team swiftly blacklisted these suspicious IP addresses, effectively preventing further unauthorized access. They also alerted the user, advising them to change their password and enable two-factor authentication to secure their account.
Application of IP Address Analysis in Fraud Management
The above case highlights the critical role of IP addresses in risk management. Companies nowadays often use IP addresses to estimate a customer’s geographic location, thus enhancing user experience by providing relevant content or services. On the other hand, fraudsters also use proxy servers to hide their real locations, engaging in malicious activities like credit card fraud or phishing. As a result, IP addresses have become more than just network identifiers; they are vital tools for detecting and preventing risks in cybersecurity.
1. Geolocation and Anomaly Detection
By analyzing the geographic locations associated with IP addresses, organizations can effectively monitor user activity and promptly detect irregular behavior. For instance, if an account usually accessed from Singapore is suddenly logged into from the United States, this deviation may be flagged as a potential security risk. Tailored security protocols can then be implemented based on regional risk assessments, enabling organizations to address global threats with greater precision.

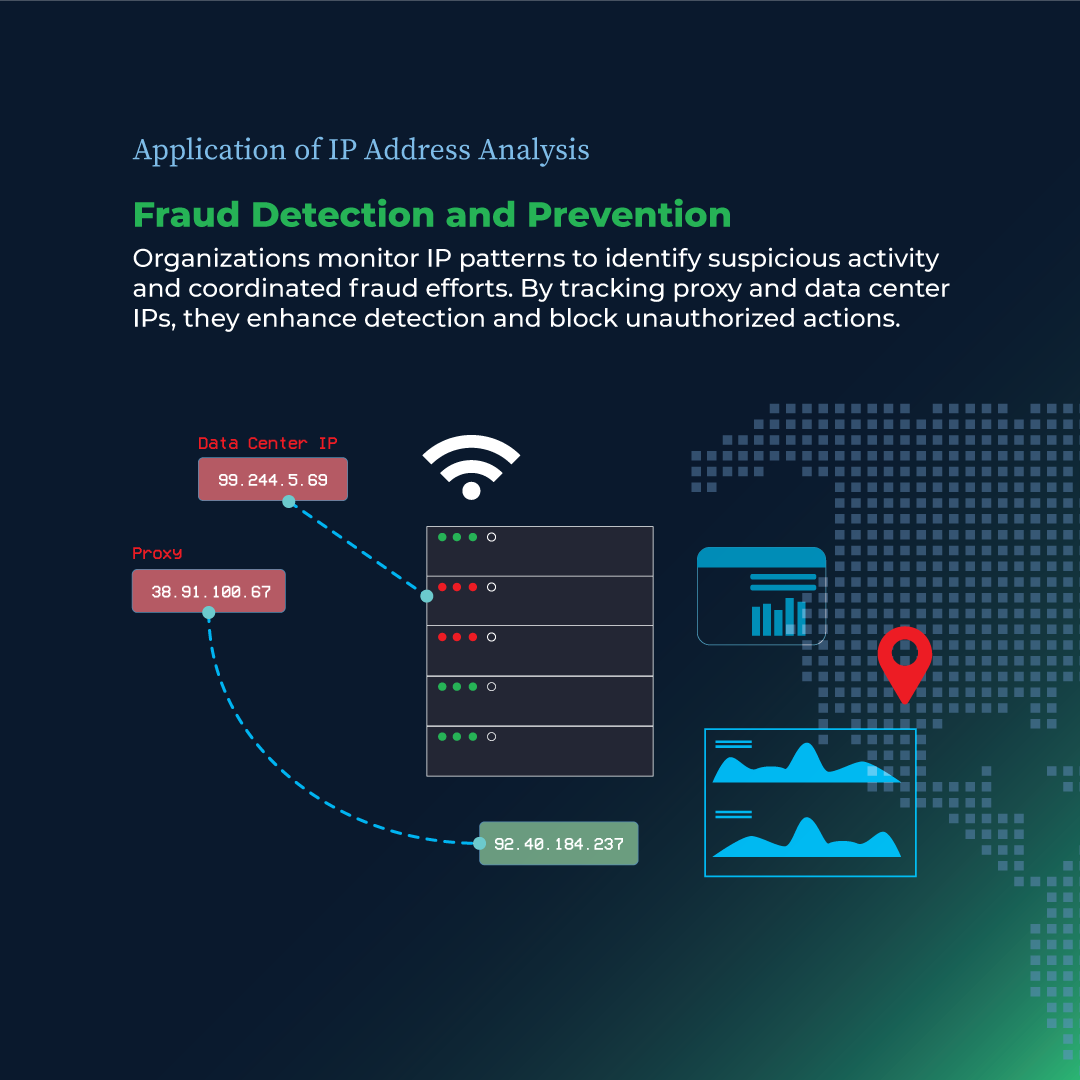
2. Fraud Detection and Prevention
Cybercriminals frequently utilize proxy servers or data center IPs to conceal their true locations and conduct fraudulent activities, such as generating multiple fraudulent accounts. By examining patterns and connections between IP addresses, organizations can identify indicators of coordinated fraud efforts, allowing for more effective threat mitigation. Continuous monitoring of proxy and data center IPs also enhances the ability to detect and block unauthorized activities, thereby fortifying platform security.
3. IP Blacklisting and Risk Scoring
The development of blacklists containing IP addresses associated with malicious activity is a fundamental automated defense against known threats. Additionally, implementing dynamic risk scoring based on an IP address’s historical activity, geographic data, and frequency of use enhances the system’s capability to make informed, real-time decisions regarding potential security risks.

4. Network Analysis and Fraud Ring Detection
By integrating IP address data with other user identifiers, such as device fingerprints and contact information, organizations can uncover hidden connections between users and detect organized fraud rings. This comprehensive analysis aids in dismantling coordinated cybercriminal operations, further strengthening security measures.

Leveraging Tools for Enhanced IP Address Analysis
To make the most of IP address data, organizations can leverage specialized tools like IP Risk Persona, a comprehensive solution developed through a strategic partnership between TrustDecision and IPLL. IP Profiles combines advanced real-time data analysis, IP reputation scoring, and anomaly detection to provide a robust defense against fraudulent activities. By analyzing IP addresses in conjunction with user behavior and historical data, this solution can quickly identify suspicious patterns and high-risk IPs, helping organizations prevent unauthorized access and fraud.
Read more about IP Risk Persona.
In A Nutshell
As cybersecurity threats become more sophisticated, the strategic use of IP addresses analysis in risk management has become critical than ever. By leveraging real-time monitoring and advanced data analytics, organizations can swiftly detect and mitigate abnormal behaviors, significantly reducing the window of opportunity for malicious activities. IP addresses not only facilitate the identification of fraudulent actions but are also integral to developing robust and adaptive risk management frameworks. In this context, IP addresses are a critical component of cybersecurity, essential for safeguarding digital infrastructures and preserving the integrity of user data.












