Key Takeaways
- Identity fraud is rising as more activity moves online, with consumers and businesses losing billions and spending hours resolving incidents.
- Fake registrations, account takeover, credential theft and social engineering now target banking, fintech, mobility, e-commerce and other digital services.
- Device fingerprinting strengthens identity fraud protection and helps in protecting digital identities by combining device recognition, behavioural signals and continuous authentication with existing eKYC and MFA.
- TrustDecision’s Device Intelligence links account, IP and device intelligence to detect abnormal frequencies, location inconsistencies and merchant anomalies in real time.
- For banks and digital platforms, device fingerprinting delivers the most value when integrated with enterprise fraud suites, identity verification and transaction monitoring as part of a unified, AI-powered identity fraud solutions stack.
What Is Identity Fraud and Why Is It Growing?
Identity fraud involves the deceptive use of someone else’s personal information—or a completely fabricated identity—for financial gain. It spans everything from card fraud and account takeover to sophisticated synthetic identity abuse.
Recent data shows just how quickly the problem is growing. The U.S. Federal Trade Commission reports that U.S. consumers lost about USD 12.5 billion to fraud in 2024, a 25% increase over 2023, with more than 1.1 million identity theft reports in a single year.
Meanwhile, a 2024 synthetic identity fraud toolkit from the Federal Reserve Banks estimates that synthetic identity fraud losses reached roughly USD 35 billion in 2023 and continue to grow as criminals increasingly weaponise generative AI to scale “Frankenstein” identities.
Common types of identity fraud include:
- Fake registration
- Fraudsters create new accounts using stolen, fabricated or synthetic identities.
- Fraudsters create new accounts using stolen, fabricated or synthetic identities.
- Account takeover (ATO)
- Attackers gain unauthorized access to existing accounts and act as the legitimate user, often after phishing or SIM-swap attacks. According to an FBI Internet Crime Complaint Center public service announcement on account takeover fraud, more than 5,100 ATO complaints and over USD 262 million in reported losses were recorded in 2025 alone.
- Attackers gain unauthorized access to existing accounts and act as the legitimate user, often after phishing or SIM-swap attacks. According to an FBI Internet Crime Complaint Center public service announcement on account takeover fraud, more than 5,100 ATO complaints and over USD 262 million in reported losses were recorded in 2025 alone.
- Credential theft
- Stolen usernames, passwords and one-time codes are reused across platforms to break into payment, wallet or banking accounts.
- Stolen usernames, passwords and one-time codes are reused across platforms to break into payment, wallet or banking accounts.
- Social engineering
- Phishing emails, fake call-center scams, deepfake voice calls and cloned websites trick users into handing over sensitive information.
Identity fraud protection therefore, has to defend both the person and the device, across the entire customer journey—from onboarding to every login and transaction.
Want a deeper dive into synthetic identity abuse? Read:
- What Is Synthetic Identity Fraud?
- Synthetic Identity Fraud Detection Challenges & AIGC Opportunities
How Does Device Fingerprinting Prevent Identity Fraud?
Device fingerprinting collects and analyzes unique attributes and behaviours of a device to build a persistent, privacy-aware device identity. This digital fingerprint helps verify whether the device using an account today looks consistent with its past behaviour—or if something suspicious has changed.
In modern fraud platforms, device data is not used in isolation. Device ID, behavioural biometrics, location intelligence and eKYC data are treated as core inputs into a holistic fraud portfolio, not just optional add-ons.
a. Device Recognition: Is This a Trusted Device?
Device fingerprinting helps you recognise returning devices with high accuracy by analysing:
- Hardware and OS attributes
- Browser and SDK information
- Network attributes (e.g., IP, ISP)
- Timezone, language, screen and other environment features
This allows platforms to:
- Fast-track trusted devices with lower friction.
- Challenge unfamiliar or risky devices with step-up checks (OTP, biometric, document verification, etc.).
- Identify device farms, emulators and automation tools commonly used in fraud operations.
For a deeper look at how device fingerprinting intersects with privacy, trust, and emerging use cases beyond fraud prevention, read Device Fingerprinting: Privacy, Trust, and New Applications
b. Behavioral Analysis: Is the Device Acting Normally?
Device fingerprinting can be combined with behavioral patterns such as:
- Typing speed and rhythm
- Mouse or touch gestures
- Navigation paths and session length
- Device and account login frequency
Unusual spikes—such as hundreds of sign-ups from the same device cluster or aggressive login bursts—raise the risk score and trigger extra verification.
c. Fraud Detection: Does This Device Match Known Fraud Patterns?
Device fingerprints help detect identity fraud by:
- Comparing devices against known high-risk clusters (e.g., devices tied to previous chargebacks, promotion abuse or mule accounts).
- Identifying shared devices used across multiple unrelated identities, suggesting synthetic identity farms or organized rings.
- Correlating IP, device, account and merchant behavior to expose hidden money-laundering networks.
This aligns with broader industry movement toward enterprise-wide fraud detection platforms that can connect multiple signals (device, identity, transaction, behavior) across channels.
To see how these trends are reshaping bank strategies, read Fraud Detection in Banking: 2025 Future Trends & Predictions.
d. Continuous Authentication: Protecting Sessions, Not Just Logins
Unlike one-time authentication at login, device fingerprinting enables continuous authentication during the entire session:
- Detects mid-session anomalies such as impossible travel, risky VPNs or sudden device changes.
- Flags high-risk operations (e.g., password reset, bank-account change, large top-up) for real-time challenge.
- Supports friction-right flows, where genuine users enjoy seamless access while risky devices are slowed or blocked.
When combined with solutions like TrustDecision’s Account Protection and Fraud Management, device fingerprinting becomes a core layer in identity fraud protection, powering smarter risk scoring and fewer false positives.
For a technical breakdown of how device fingerprints are generated and maintained, explore:
- How Device Fingerprints Work in Identity Fraud Scenarios
- Generating Device Fingerprint In-House: Challenges and Solution
Use Case: How TrustDecision’s Device Intelligence Protects an EV Charging Network from Identity Fraud
One real-world deployment of Device Intelligence from TrustDecision involves a leading EV charging network for professional drivers in Asia. This use case shows how identity fraud, promotion abuse and money laundering can hide inside seemingly low-risk top-ups and charging sessions—and how Device Intelligence makes those risks visible.
What Challenges Did the EV Charging Network Face?
The EV charging platform offers online top-ups and payments through apps and mini-programs. As volumes grew, several risk patterns emerged:
- Fraudulent registrations: New accounts opened using stolen, fake or synthetic identities.
- Bulk logins and scripted behaviour: High-frequency login attempts concentrated on a small number of devices.
- Abuse of online recharge flows: Top-ups used for cash-out schemes and mule activity rather than genuine charging.
- Suspicious merchant behaviour: Small merchants showing transaction volumes far beyond their physical footprint.
Taken together, these risks underscore why platforms like this EV charging network need device-level intelligence as a core layer of their identity fraud protection strategy.
What Potential Risks and Losses Did the Platform Face?
Without robust identity fraud protection, the platform faced:
- Direct revenue loss from fraudulent top-ups, refunds and chargebacks
- Regulatory penalties or business suspension due to AML breaches
- Marketing waste, as incentives and promotions were captured by fraud rings instead of genuine users
- Brand and reputation damage, undermining trust among legitimate drivers, merchants and partners
This context underscores why platforms like the EV charging network need device-level intelligence as part of their identity fraud protection strategy.
How Did Device Intelligence Mitigate Identity Fraud and Money Laundering?
TrustDecision’s Device Intelligence delivered a multi-layered device fingerprinting and risk-decisioning solution tailored to the EV charging platform’s ecosystem.
1. Account, IP and Device Frequency Analysis
Device Intelligence correlated:
- Account → Device relationships
- Device → IP clusters
- Device → Transaction frequencies
This made it possible to:
- Flag device farms used across hundreds of accounts.
- Detect abnormal login and recharge frequencies.
- Identify shared wallets or device clusters used to cycle funds through the platform.
These capabilities are consistent with best practices recommended in industry guidance, where transaction monitoring, device ID and identity verification should be orchestrated through a single fraud platform.
2. Multi-Factor Location Verification
To combat online and offline money-laundering schemes, Device Intelligence introduced multi-factor location verification by cross-referencing:
- User’s registered location
- Device location and IP intelligence
- Merchant and transaction location
Examples of high-risk patterns included:
- Drivers topping up from locations far away from their typical charging routes.
- Inconsistent device locations compared with declared merchant branches.
- Repeated high-value top-ups followed by low-value on-site consumption, a classic sign of mule or layering activity.
Risky sessions could then be:
- Blocked in real time
- Sent to manual review
- Challenged with additional eKYC or payment verification
3. Specialized Models and Machine Learning
Device Intelligence used specialized ML models and rules tuned to the EV charging context. These models:
- Continuously learned from new fraud patterns
- Updated risk thresholds as attacker behavior changed
- Combined device fingerprints, behavioral relationships and transaction flows into a unified risk score
This mirrors the direction of modern banking fraud platforms, where ML models are retrained frequently and orchestrated alongside business rules to keep up with evolving attack vectors.
4. Merchant Behavior Detection
Device Intelligence also analysed merchant-side behavior, focusing on:
- Transaction volume vs. outlet size
- Unusual patterns in voucher redemptions or top-ups
- Merchant accounts repeatedly linked to high-risk devices
Red flags included small merchants with disproportionately high transaction volumes, inconsistent operating hours, or cross-device anomalies indicative of mule hubs.
These insights helped the platform enforce risk-based merchant monitoring, aligned with broader enterprise fraud management strategies such as TrustDecision’s ARGUS® Fraud Management Platform.
What Results Did the EV Charging Platform Achieve?
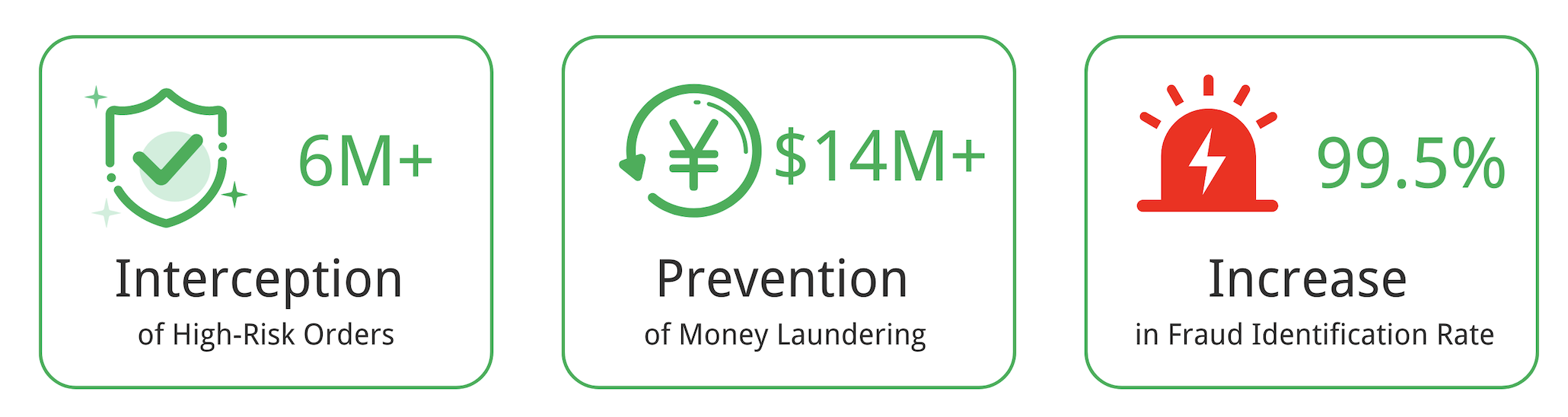
By combining device fingerprinting with multi-factor analysis and specialized models, the platform achieved significant outcomes:
- Interception of High-Risk Orders
More than 6 million high-risk orders were intercepted before completion, preventing substantial financial loss.
- Prevention of Large-Scale Money Laundering
Device Intelligence helped detect and stop money-laundering attempts involving over USD 14 million in suspicious transactions.
- Enhanced Fraud Detection
The solution achieved an estimated 99.5% fraud identification rate against illicit transactions executed by organized criminal networks, significantly boosting platform security and trust.
In summary, these results align with wider banking trends where fraud teams are consolidating device, transaction and identity signals into customer-centric, cross-channel platforms for better detection and lower false positives.
For organizations seeking to replicate these outcomes across multiple channels, TrustDecision’s Fraud Management and Account Protection solutions provide a broader framework that extends beyond a single use case.
How Should Businesses Approach Identity Fraud Protection Today?
In a digital ecosystem where customers use multiple devices, channels and payment methods, identity fraud protection is no longer about a single control. It is about orchestration:
- Combine eKYC and identity verification with device fingerprinting and behavioral biometrics.
- Embed continuous authentication into logins, top-ups, payments and account changes.
- Use centralized fraud platforms like ARGUS®Fraud Management Platform to unify scoring, monitoring and case management across products and regions.
- Prepare for GenAI-driven fraud by pairing large-scale analytics with responsible AI governance and banking-grade controls.
To understand how generative AI is changing identity fraud and what that means for fraud teams, read Generative AI and the Intensified Identity Fraud Threat.
Conclusion: Strengthen Identity Fraud Protection with Device Intelligence
As digital interactions multiply across channels and devices, identity fraud protection must be continuous, contextual and device-aware. Device fingerprinting is a critical layer in this defense, helping businesses distinguish trusted users from high-risk devices in milliseconds—without overwhelming genuine customers with friction.
With TrustDecision’s Device Intelligence, organizations gain:
- Stable, high-fidelity device fingerprints
- Real-time correlation across accounts, IPs, devices and merchants
- Proven results in intercepting high-risk orders and blocking large-scale money laundering attempts
Ready to reduce identity fraud and account takeover?
Talk to us today to see how TrustDecision’s Device Intelligence, eKYC/Identity Verification and centralized Fraud Management can be tailored to your banking, fintech, mobility or e-commerce journeys.
Our team can help you design a phased roadmap that delivers quick wins—such as securing logins and top-ups—while laying the foundation for long-term, enterprise-wide identity fraud protection.
FAQs
1. How does device fingerprinting improve identity fraud protection compared to traditional methods?
Traditional methods rely heavily on static credentials (passwords, SMS OTPs) and one-time checks at login or onboarding. Device fingerprinting adds:
- Persistent, privacy-aware device identity
- Session-level behavioral and environmental signals
- Real-time comparison against historical patterns and known risk clusters
This makes it much harder for attackers to reuse stolen credentials or operate large-scale fake account farms without being detected.
2. Is device fingerprinting compliant with privacy regulations?
When implemented correctly, device fingerprinting can be privacy-preserving:
- No need to store sensitive personal content such as messages or photos
- Fingerprints can be pseudonymised and rotated based on policy
- Risk signals are used for security and fraud prevention, which is typically recognized as a legitimate interest under many data-protection frameworks
TrustDecision works with customers to align device intelligence with local privacy laws and internal compliance requirements.
3. What types of fraud can Device Intelligence help prevent?
Device Intelligence supports identity fraud protection across multiple scenarios, including:
- Fake registrations and synthetic identity onboarding
- Account takeover attacks and credential-stuffing campaigns
- Promotion abuse, top-up fraud and incentive misuse
- Money-laundering patterns involving device clusters, mule accounts and suspicious merchants
When paired with TrustDecision’s Identity Verification and Fraud Management solutions, it becomes part of a full end-to-end digital identity defense stack.
4. How does Device Intelligence integrate with my existing fraud or KYC systems?
TrustDecision’s Device Intelligence is designed to integrate via SDKs and APIs into web, mobile app and backend environments:
- Client-side SDKs collect device attributes and risk signals.
- Risk scores and labels are sent to your decision engine, fraud platform or case-management tools.
- It can plug into broader platforms like ARGUS® for centralized orchestration and rule management.
This allows you to enhance existing KYC, onboarding and transaction monitoring processes without rewriting your entire stack.
5. How does TrustDecision support identity fraud protection across different industries?
TrustDecision’s platform is built for finance, digital commerce, mobility, gaming, travel and more.
- Financial institutions can use Device Intelligence to secure online banking, wallets, BNPL and lending journeys.
- Mobility and EV platforms can monitor driver, rider and merchant behavior at the device level.
- E-commerce and marketplaces can detect fake accounts, promo abuse and mule networks.
Each deployment is tuned with industry-specific rules, data sources and workflows.
6. How can we get started with Device Intelligence and TrustDecision’s identity fraud protection stack?
You can:
- Start with a pilot deployment focused on high-impact journeys such as account opening, login, or top-up flows.
- Combine Device Intelligence with Account Protection to secure logins and session activity.
- Extend coverage with Fraud Management and Identity Verification for end-to-end defense.
To see how this works in practice, explore TrustDecision’s case studies page, including the EV charging network example featured in this article.









